If you’re a mid-sized business, here’s a hard truth: you are squarely in the crosshairs.
For years, there has been a lingering belief that cybercriminals only go after big-name enterprises with sprawling infrastructures and deep pockets. But the data tells a different story. According to IBM’s 2024 Cost of a Data Breach Report, mid-sized companies now face average breach costs of $3.5 million. Why? Because attackers know that mid-sized often means under-resourced, under-defended, and overwhelmed.
The reality is, you do not have to be high-profile to be high-risk. If you store sensitive data, process transactions, rely on cloud applications, or have remote employees, you are a target.
And in 2025, relying on firewalls and antivirus software alone is not enough. Reactive security models, the kind that only kick in once something has already gone wrong, leave you exposed. The threat landscape has evolved, and so should your defense strategy.
This blog post is your guide to what modern managed cybersecurity looks like for mid-market companies. What to expect. What to ask. And how to build a defense that is not just technical, but strategic. Ready? Let’s get into it.
What Counts as Cybersecurity Services in 2025?
Cybersecurity isn’t just antivirus and a strong password policy anymore. In 2025, it’s a layered ecosystem—built to prevent, detect, and respond to threats in real time.
Modern cybersecurity services include:
- MDR (Managed Detection and Response): Real-time threat detection and expert-led remediation
- EDR (Endpoint Detection and Response): Protects workstations, laptops, and mobile devices from advanced attacks
- SIEM (Security Information and Event Management): Centralized log collection, analysis, and anomaly detection
- Firewall Management: Continuous monitoring, updates, and rule enforcement across your perimeter
- Patching and Vulnerability Management: Proactively closing gaps before attackers find them
- Policy Support: Documentation, compliance alignment, and user training to reduce risk at every level
What separates modern cybersecurity from older, break/fix models is the approach. A break/fix mindset waits until something goes wrong. A managed model is always working in the background, hunting for threats, closing vulnerabilities, and keeping your systems in check—before a breach ever happens.
Here’s how the typical support stacks up:
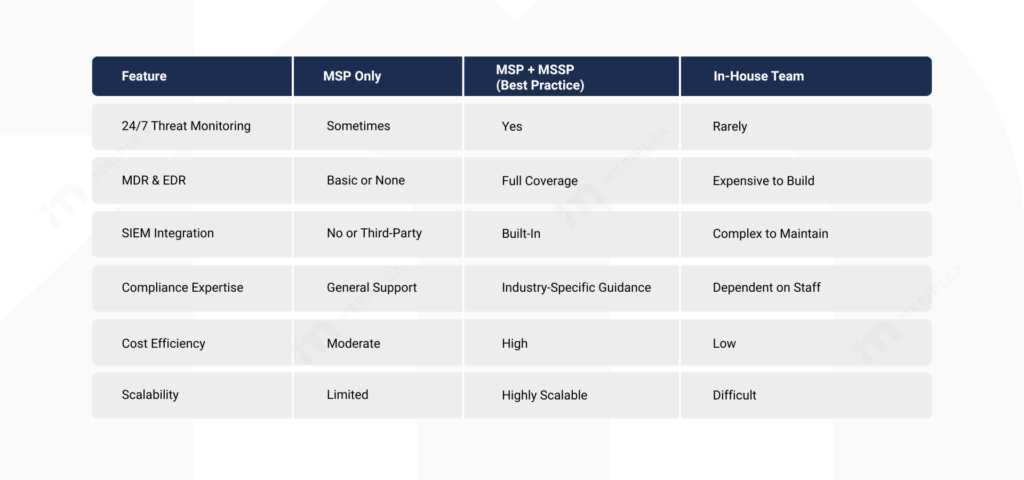
If your current provider doesn’t offer these services—or if your internal team is struggling to keep up—it may be time to reassess what cybersecurity really means for your business.
Because in 2025, it’s not just about reacting fast. It’s about staying ahead.
See What Gaps You're Missing
Standalone Cybersecurity vs. Bundled with IT Services: What’s Right for You?
Cybersecurity can live on its own or as part of a broader IT strategy. The right setup depends on your environment, risk profile, and internal capacity.
When standalone cybersecurity makes sense:
Some mid-market companies need a dedicated security partner. This is especially true if you’re in a highly regulated industry, managing sensitive data, or dealing with complex multi-cloud or hybrid environments. A standalone MSSP (Managed Security Services Provider) brings specialized focus. You get deeper threat intelligence, incident response expertise, and direct alignment with frameworks like HIPAA, PCI, or NIST.
If you’re already working with an internal IT team or another MSP, a standalone security partner can fill critical gaps without restructuring your whole environment.
When cybersecurity is bundled with IT services:
For many mid-market companies, the most practical and cost-effective option is working with an MSP that offers both IT support and fully managed security. You reduce vendor sprawl, simplify billing, and gain a more integrated view of your environment. The right partner will handle everything from help desk tickets to threat detection within one platform—and they’ll ensure your systems and users are protected at every layer.
What to look for, no matter which model you choose:
- 24/7 monitoring and response. Threats don’t stick to business hours, and neither should your provider.
- Clear SLAs. You need to know how fast someone will respond—and how issues are escalated.
- Compliance support. Whether you’re governed by HIPAA, CMMC, or the FTC Safeguards Rule, look for a partner who’s already helping clients meet those standards.
- Tool integration. Cybersecurity doesn’t work in a silo. Make sure your partner’s tools play well with your systems, devices, and users.
At the end of the day, the right cybersecurity model is the one that protects your business without slowing it down. Whether you bundle services or go best-of-breed, make sure your team, your systems, and your reputation are covered.
The Biggest Risks Mid-Market IT Leaders Face Today
For mid-sized companies, the threat landscape isn’t just growing—it’s outpacing internal capacity to manage it. Most IT leaders in this space are being asked to do more with less while attackers are getting faster, smarter, and more opportunistic.
Here are the most pressing risks we’re seeing across the mid-market:
1. Lack of Dedicated Security Staff
Unlike enterprise organizations, most mid-sized companies don’t have a full-time CISO or a dedicated security team. That means IT teams are managing everything from user access and infrastructure to incident response and compliance reporting—often without the time, tools, or headcount to do it all effectively.
According to Forrester’s 2024 Mid-Market Threat Report, 58% of mid-sized firms cite limited security staffing as their top barrier to improving protection.
2. A Growing Attack Surface
The shift to hybrid work, increased reliance on SaaS tools, and the rise of connected devices have expanded the digital footprint of every business. Every app, endpoint, and remote login is a potential entry point for attackers.
The Verizon Data Breach Investigations Report confirms it—phishing, stolen credentials, and misconfigurations are still the top causes of breaches, and they thrive in fast-moving, lightly resourced environments.
3. Mounting Compliance Risk
The shift to hybrid work, increased reliance on SaaS tools, and the rise of connected devices have expanded the digital footprint of every business. Every app, endpoint, and remote login is a potential entry point for attackers.
The Verizon Data Breach Investigations Report confirms it—phishing, stolen credentials, and misconfigurations are still the top causes of breaches, and they thrive in fast-moving, lightly resourced environments.
How to Evaluate a Cybersecurity Provider
Choosing a cybersecurity partner isn’t just about checking boxes on a service list. It’s about finding a team that’s proactive, accountable, and aligned with your long-term goals.
Here’s what to look for when evaluating providers:
Core Services Should Be Table Stakes
If a provider doesn’t offer the essentials, they’re not equipped to protect your business. At a minimum, they should include:
- 24/7 threat detection and response
- Endpoint protection (EDR/MDR)
- Security assessments and vulnerability scans
- User training and phishing simulations
- Policy creation and compliance support
These aren’t “nice to haves.” They’re the foundation.
Build a Strategy That Fits Your Business
Look for Real Transparency
You need to know what’s happening behind the scenes. A good provider will offer:
- Clear SLAs with defined response and resolution times
- Monthly or quarterly reports on threats, incidents, and system health
- Documentation you can share with leadership, auditors, or regulators
If you’re relying on someone to protect your environment, you should never be in the dark.
Strategic Support Matters
The best cybersecurity providers act like an extension of your business. That means offering virtual CISO (vCISO) support to help:
- Align security investments with business risk
- Prepare for audits or insurance renewals
- Build roadmaps for maturity and compliance
Cybersecurity isn’t just IT—it’s business risk management. Your provider should think like an executive, not just a technician.
Questions to Ask Every Cybersecurity Vendor
Whether you’re vetting a new MSSP or reassessing your current one, use these questions to dig deeper:
- What’s your average time to detect and respond to a threat?
- Do you offer documented SLAs and regular reporting?
- Can you help us prepare for HIPAA, PCI, or other compliance audits?
- Who handles escalations and remediation during an incident?
- How do you stay current with evolving threats and technologies?
- Do you provide user training and simulated phishing?
- What visibility will we have into our environment?
The goal isn’t just to find someone who can install tools—it’s to find a partner who can help you build resilience, scale securely, and sleep better at night.
Because when it comes to cybersecurity, you want proactive strategy. Not reactive clean-up.
Cybersecurity Budgeting for Mid-Market Companies
Cybersecurity spending used to feel like a black hole—expensive, unpredictable, and hard to quantify. For mid-market companies trying to stretch limited budgets, this can make proactive investment feel like a luxury instead of a necessity.
But the game is changing. Today, cybersecurity is shifting from capital expense to operating expense. That distinction matters.
CAPEX vs. OPEX: What’s the Difference?
Building an in-house security operation typically falls under CAPEX. You’re buying firewalls, hiring full-time security staff, and making large upfront investments in infrastructure. That’s a heavy lift for most mid-sized businesses.
Outsourcing, on the other hand, falls under OPEX. It’s a predictable monthly cost that includes monitoring, response, patching, and policy support—all bundled into a single line item. You’re not paying for hardware or salaries. You’re paying for outcomes.
Why That Matters:
Building an in-house security operation typically falls under CAPEX. You’re buying firewalls, hiring full-time security staff, and making large upfront investments in infrastructure. That’s a heavy lift for most mid-sized businesses.
Outsourcing, on the other hand, falls under OPEX. It’s a predictable monthly cost that includes monitoring, response, patching, and policy support—all bundled into a single line item. You’re not paying for hardware or salaries. You’re paying for outcomes.
Real-World Impact:
According to Deloitte’s 2024 Global Outsourcing Survey, companies that outsourced cybersecurity functions saw a 26% reduction in security operating costs and a 40% improvement in time-to-detection. That’s not just savings—it’s resilience.
Managed security services allow you to focus your internal IT budget on innovation while letting the heavy lifting of protection, compliance, and monitoring sit with a partner who’s built for it.
In a world where breach costs are climbing and security talent is hard to find, this kind of budgeting shift can be the difference between progress and firefighting.
Meriplex’s Approach to Mid-Market Cybersecurity
At Meriplex, we know that mid-market businesses face enterprise-level threats without enterprise-sized IT teams. That’s why our cybersecurity approach is built specifically for the realities of growing, resource-conscious organizations.
We offer layered, fully managed cybersecurity services designed to close your most critical gaps while fitting seamlessly into your existing environment. From proactive threat detection to real-time incident response, we help you stay ahead of threats—without overextending your team or your budget.
What our cybersecurity stack includes:
- MDR and EDR: Real-time threat detection, isolation, and response across all endpoints
- SIEM Integration: Centralized monitoring and analysis to catch subtle threats
- Firewall and Perimeter Security: Fully managed, monitored, and updated
- Patch and Vulnerability Management: Ongoing updates to keep your systems secure and compliant
- Compliance Support: Aligned to HIPAA, PCI, CCPA, FTC Safeguards Rule, and more
- User Awareness Training: Reduce risk from phishing and social engineering with built-in education tools
We work with your current tech stack—not against it. Whether you’re running Microsoft, Google Workspace, AWS, or hybrid infrastructure, we plug in, monitor, and secure everything without disruption.
The results speak for themselves:
- Increased uptime with faster detection and fewer false positives
- Better compliance with policy templates, audit prep, and reporting
- Predictable costs with flat-rate pricing and no surprise charges
- Happier teams who spend less time chasing down tickets and more time focused on the work that moves the business forward



