Today’s threats don’t just crash systems. They derail operations, stall revenue, and shake customer trust. According to IBM’s 2024 Cost of a Data Breach Report, the average breach for a small or mid-sized business costs $3.5 million. And that’s just the financial impact. The reputational damage is harder to measure, but even more difficult to repair.
For growing businesses, strategic cybersecurity budgeting isn’t optional. It’s how you protect the business you’ve worked hard to build. It’s also how you position your company for sustainable growth.
This guide walks through what to consider when setting a cybersecurity budget, how to align it with your business goals, and where most companies make the wrong assumptions.
How Much Should You Spend on Cybersecurity?
Let’s start with the question every executive asks: what’s a reasonable cybersecurity budget?
Most growing businesses allocate 7 to 12% of their total IT budget toward cybersecurity, depending on their risk exposure and compliance landscape. But averages only go so far. A more useful approach is to budget based on your actual business needs and risk profile.
Here are a few factors that should guide your spend:
- Regulatory requirements
If you’re in a regulated industry like healthcare, finance, or retail, frameworks like HIPAA, PCI-DSS, or GLBA may dictate minimum standards for security. Failing to meet them can lead to hefty fines and legal liability.
- Remote or hybrid workforce
The more dispersed your team, the more endpoints and access points you need to protect. VPNs, endpoint detection, and identity access management add to both the cost and the complexity.
- Customer data sensitivity
If you store or process customer information—especially health or financial data—your tolerance for risk should be low. A single breach can erode trust that took years to build.
- Cyber insurance requirements
Insurers are tightening their coverage standards. To even qualify for a policy (or keep premiums reasonable), you may need to prove you have things like multifactor authentication, continuous monitoring, and a written incident response plan in place.
Budgeting isn’t just about the number. It’s about aligning spend with risk, exposure, and the outcomes that matter most to your business.
Build a Smarter Cybersecurity Budget
OPEX vs. CAPEX: Understanding Where Cyber Costs Fall
If you’re responsible for budgeting, you already know not all expenses are created equal. That’s especially true in cybersecurity, where the lines between capital expenses (CAPEX) and operating expenses (OPEX) are getting blurrier by the year.
The Basics: What Goes Where
CAPEX covers long-term investments—hardware, infrastructure, and anything you depreciate over time. In cybersecurity, this usually includes:
- On-premise firewalls
- Security appliances
- Network segmentation hardware
- Infrastructure upgrades tied to physical assets
OPEX, on the other hand, refers to your ongoing operational costs. These are typically subscription-based services or recurring support functions like:
- Managed Detection and Response (MDR)
- Outsourced Security Operations Centers (SOCs)
- Cybersecurity software licensing (EDR, SIEM, etc.)
- Compliance audits and penetration testing
Why the Distinction Matters
The difference between CAPEX and OPEX isn’t just accounting trivia. It directly affects cash flow, tax strategy, and the speed of decision-making.
- Cash flow: OPEX models tend to be easier on your cash reserves. You’re paying a predictable monthly fee rather than writing a six-figure check upfront.
- Taxes: OPEX spend is typically 100% deductible in the year it’s incurred. CAPEX, by contrast, is depreciated over time—often across a five- or seven-year schedule.
- Approval cycles: Getting a large CAPEX project through the finish line can involve more red tape, especially in organizations where capital budgets are locked in once a year. OPEX gives you more agility to pivot with changing risk levels or business priorities.
The Shift Toward Cyber-as-a-Service
Over the last five years, we’ve seen a major trend toward Cybersecurity-as-a-Service models. There’s a reason for that. Businesses want security outcomes, not just tools. They want protection that scales with growth, adapts to new threats, and doesn’t require hiring a full in-house team of experts.
Moving more security costs into the OPEX column allows companies to:
- Stay nimble with tech upgrades
- Scale resources up or down as needed
- Access higher-tier security expertise than they could staff internally
For most mid-market businesses, a hybrid model makes the most sense. Use CAPEX for your core infrastructure when necessary, but lean into OPEX for services that evolve with your environment.
The bottom line? Don’t just ask what a security investment costs. Ask how it fits into your financial strategy, and how quickly it can adapt to your risk landscape.
A Cybersecurity Maturity Framework to Guide Budgeting
Not every business needs a seven-figure security program. But every business does need a clear understanding of where they stand today—and where they’re headed.
That’s where a Cybersecurity Maturity Framework comes in. It helps align your security investments with your current capabilities, risk profile, and business goals. Without it, you risk either overspending on tools you’re not ready to operationalize, or underspending and leaving critical gaps exposed.
Here’s a simplified four-stage model to help guide your thinking:
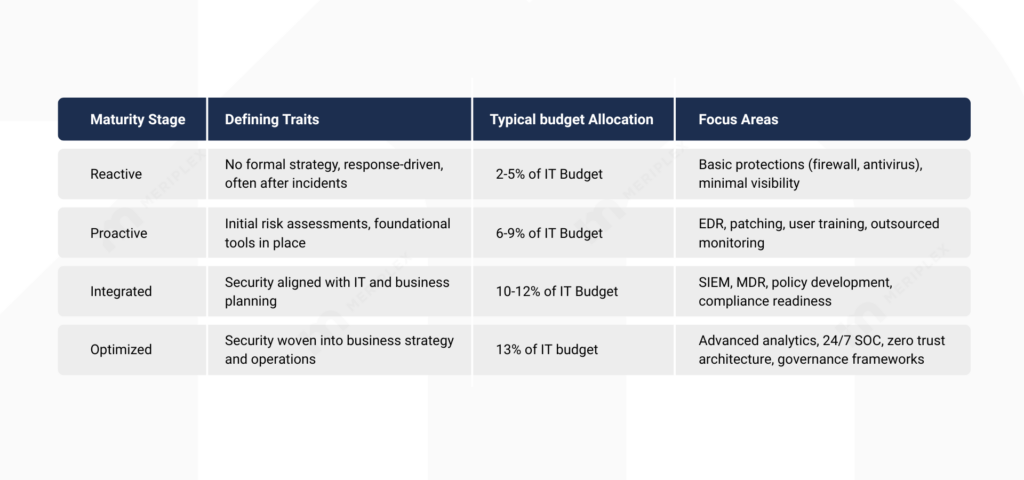
This model isn’t about checking boxes. It’s about clarity.
If you’re in the Reactive stage, your primary goal should be reducing exposure to common threats quickly and affordably. In the Proactive or Integrated stages, your budgeting should reflect a growing need for visibility, compliance, and threat response. And if you’re aiming for Optimized, you’re likely managing a complex environment that demands continuous improvement and real-time oversight.
The most effective security budgets are ones that meet you where you are—but are built with a clear path to where you want to go.
Sample Budgeting Models (With Ranges)
Cybersecurity spend isn’t one-size-fits-all. Your industry, risk profile, and stage of growth all play a role in shaping what your budget should look like—and what it needs to cover.
Below are three real-world scenarios that offer a starting point. These aren’t theoretical wishlists. They’re practical examples of what growing businesses might invest based on where they are today.
Scenario 1: High-Growth SMB with Lean IT
Company Profile
- 150 employees
- Single IT manager, no dedicated security staff
- Heavy reliance on cloud apps and remote work
Estimated Annual Cybersecurity Budget
$75K–$120K
What This Covers
- Managed Detection and Response (MDR)
- Endpoint Detection and Response (EDR)
- Email filtering and DNS security
- Basic compliance support and user training
- Annual penetration test
Primary Risks
- Phishing, credential theft, shadow IT
- Limited internal oversight and slow incident response
Takeaway: The goal here is coverage and speed. With limited in-house resources, outsourced security operations can close critical gaps without ballooning headcount.
Scenario 2: Healthcare Organization with Compliance Obligations
Company Profile
- 300 employees
- In-house IT team of 5
- Subject to HIPAA and regularly audited by insurers
Estimated Annual Cybersecurity Budget
$200K–$300K
What This Covers
- 24/7 SOC support with audit-ready reporting
- Risk assessments and HIPAA-aligned policies
- Ongoing compliance monitoring and staff training
- Secure backup and disaster recovery systems
- Email encryption and multifactor authentication
Primary Risks
- Patient data exposure, ransomware, third-party vendor risk
Takeaway: Compliance isn’t optional—and it’s not cheap to get wrong. Here, the budget must account for both ongoing risk management and documentation that satisfies regulators and insurers.
Unsure If You’re Overspending or Underprotected?
Scenario 3: Retail Business Undergoing Digital Transformation
Company Profile
- 500 employees across multiple locations
- Expanding e-commerce platform
- Migrating infrastructure to the cloud
Estimated Annual Cybersecurity Budget
$250K–$400K
What This Covers
- Cloud security posture management (CSPM)
- SIEM platform for unified threat visibility
- Web application firewall (WAF)
- Identity and access management (IAM)
- Third-party risk assessments
Primary Risks
- Customer data compromise, website downtime, supply chain vulnerabilities
Takeaway: For businesses scaling digitally, security has to move at the same pace. Budgeting here is about protecting uptime, revenue continuity, and customer trust during high-growth transitions.
These numbers will vary based on tech stack, geographic footprint, and vendor selection—but they offer a clear picture of what it takes to invest in cybersecurity the right way.
The Cost of Readiness vs. the Cost of Risk
It’s easy to see cybersecurity as a cost center—until you experience what happens without it.
Security budgets often get squeezed because they’re not tied to immediate revenue. But the truth is, failing to invest in readiness usually leads to a much larger bill later on. This is where the concept of Total Cost of Risk (TCOR) becomes a powerful budgeting tool.
TCOR includes more than just the direct cost of a breach. It factors in:
- Business downtime
- Regulatory fines
- Legal fees
- Customer attrition
- Reputational damage
- Insurance premium hikes
When you look at the numbers side-by-side, the logic becomes clear.
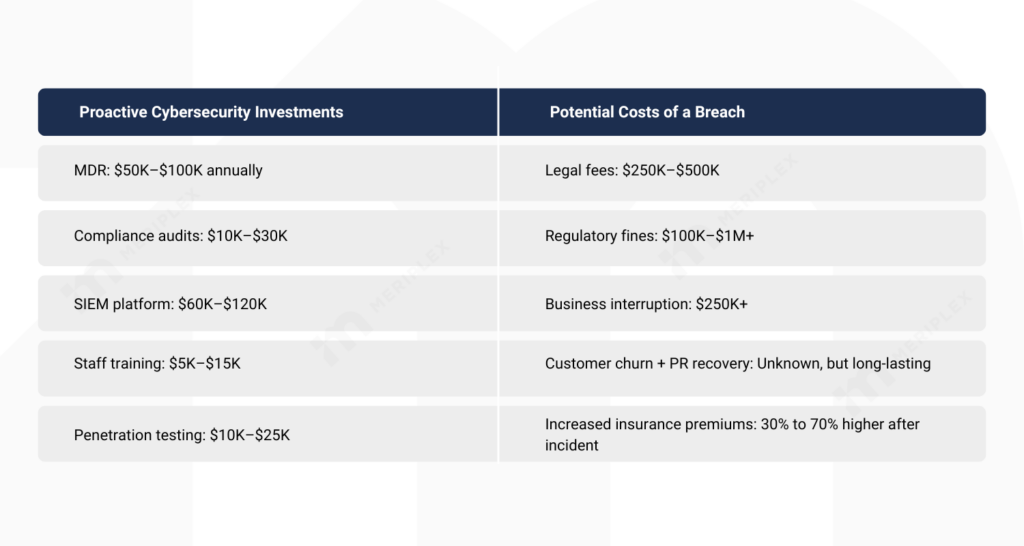
It’s not about spending less—it’s about spending smart. Readiness means making intentional investments that reduce your total exposure over time.
By using TCOR as part of your internal justification, you’re not just defending a budget—you’re demonstrating the financial impact of security decisions on the business as a whole.
In short: You can pay to be prepared, or you can pay for the aftermath. One is predictable. The other isn’t.
Top Cybersecurity Budgeting Mistakes to Avoid
Even with the best intentions, many businesses end up with cybersecurity budgets that fall short. The issue isn’t always a lack of spend. More often, it’s about spending in the wrong places.
One of the most common mistakes is relying entirely on internal IT to manage security. Even the most capable IT teams often lack the specialized training or time to stay ahead of today’s threat landscape. Cybersecurity requires a dedicated approach. Asking your generalist IT staff to handle it on top of their regular responsibilities leads to blind spots and burnout.
Another misstep is investing heavily in tools without funding the people or processes needed to use them effectively. Purchasing a top-tier endpoint solution or SIEM platform won’t make a difference if no one is actively monitoring alerts, managing updates, or fine-tuning the system. Tools without the right support create a false sense of protection and leave the business vulnerable when it matters most.
Some organizations also treat cybersecurity like a one-and-done project. They set a yearly budget, make a few purchases, and move on. But cybersecurity isn’t static. Threats evolve, your business changes, and your environment shifts. Budgeting must reflect that. It’s an ongoing investment, not a single transaction.
Finally, many leaders underestimate the cost of breach recovery. The impact goes beyond immediate response and remediation. There are legal costs, compliance penalties, brand damage, and lost business to consider. Planning a budget without acknowledging those risks is like building a house without insurance. You hope nothing goes wrong, but if it does, the financial impact can be devastating.
Avoiding these common mistakes doesn’t necessarily mean increasing your budget. It means being thoughtful about where your dollars go and aligning them with your real-world risks. Cybersecurity is a business priority, not just a technical one.
Tools to Make the Case Internally
Getting cybersecurity budget approval often requires more than data. It takes the right language, especially when presenting to the board or non-technical stakeholders.
One of the most effective ways to frame the conversation is by connecting cybersecurity to business continuity. Leaders understand the value of uptime. They understand the cost of operational disruption. When you explain that cybersecurity protects revenue flow, customer trust, and the ability to deliver services without interruption, the conversation shifts from expense to investment.
Risk avoidance is another powerful lens. Instead of asking for a tool, position the request as a measure that reduces the likelihood of costly incidents. For example, implementing MDR is not just a tech decision. It’s a way to avoid regulatory fines, insurance hikes, and the reputational damage that comes from a public breach. The more specific you can be about the risks being mitigated, the more weight your proposal will carry.
Security also deserves to be seen as a business enabler. When done well, it supports faster adoption of new technologies, smoother audits, and stronger customer confidence. It removes obstacles to growth, rather than adding friction. For businesses entering new markets, launching digital services, or navigating complex compliance environments, strong cybersecurity is a competitive advantage.
The goal is to reframe the conversation. This isn’t about fear. It’s about resilience. It’s about creating the conditions for long-term stability and growth. When you speak the language of outcomes, security becomes much easier to fund.
Optimize Spend Without Compromising Security
Next Steps: Let’s Build Your Budget Together
If you’re ready to take a more strategic approach to cybersecurity budgeting, Meriplex is here to help. We offer a free budgeting workshop designed specifically for growing businesses that want to better align their security investments with risk, growth, and operational goals.
During this session, our team will conduct a security maturity assessment to pinpoint where your business stands today. We’ll then walk you through a tailored budgeting model that aligns with your industry, compliance requirements, and IT strategy. You’ll leave with a clear, cost-justified roadmap that you can use to guide internal conversations and drive smarter decisions.
Think of it as your blueprint for reducing risk, optimizing spend, and strengthening your security posture with confidence.
Ready to get started? Let’s build it together. Request your cybersecurity budgeting workshop today.
Want to understand the full spectrum of modern cybersecurity services? Explore the cybersecurity services you need in 2025 to see how layered, proactive protection can support your business at every stage.



